eMCP desoldering is a high-end hardware hacking method used when software access is blocked, since eMCP packages combine both NAND storage and DRAM in a single BGA chip. By removing the package, researchers can dump raw data, bypass secure boot, or attempt forensic recovery. Other chip types also come into play: eMMC and UFS (storage-only) are common BGA targets for firmware extraction, while uMCP integrates UFS with RAM and raises the complexity further. LPDDR RAM itself isn’t directly useful for dumping but can be attacked through side channels like cold boot. PoP packages, where the CPU and memory are stacked, add another layer of difficulty for direct analysis. On the easier side, raw NAND or NOR flash chips sometimes appear in TSOP, SOIC, or WSON packages, and SPI NOR boot flash in SOIC-8 is especially hacker-friendly since it can be clipped or desoldered for straightforward reads. In practice, this means modern smartphones and IoT devices force hackers to deal with challenging BGA chip-off work, while older or low-end hardware often exposes more accessible packages that are quicker to attack.
Note: This blog is completely for educational purposes only. We have chosen the target device Amazon Firestick 1st Generation which has the eMCP.
| Chip Type | Definition / What It Is | Hacker’s POV |
|---|---|---|
| eMMC (embedded MultiMediaCard) | Storage chip (NAND + controller) in BGA. Used in phones, IoT, embedded systems. | Common chip-off target for firmware dumps. |
| eMCP (embedded Multi-Chip Package) | Combines NAND storage + DRAM in one BGA package. Space-saving design for mobile/IoT. | Harder to rework; used for deep data extraction and bypassing secure boot. |
| UFS (Universal Flash Storage) | Faster, newer storage standard than eMMC. Always BGA. | Requires advanced adapters/programmers; tougher than eMMC. |
| uMCP (UFS Multi-Chip Package) | Combines UFS storage + RAM in one BGA. | Even more complex; tricky for hackers to separate functions. |
| LPDDR / DRAM Components | Low-power DDR RAM chips, memory only. | Not for dumping, but exploitable with cold boot or fault attacks. |
| PoP / ePoP (Package on Package) | CPU and RAM stacked in a single BGA package. | Extremely hard to access; usually avoided unless advanced probing. |
| Raw NAND Flash | Bare NAND storage without controller. Can be BGA or TSOP. | Useful for direct dumps but needs ECC handling. |
| NOR Flash | Smaller, faster storage, often used for boot firmware. Comes in SOIC, TSOP, or BGA. | Good for bootloader extraction or reverse engineering. |
| SPI NOR Flash | Serial NOR flash, often in SOIC-8 or WSON packages. Stores BIOS/boot code. | Hacker-friendly: easy to clip or desolder and dump. |
| Design-In SSD | Embedded solid-state drives (NAND + controller in SSD form factor). | Easy to interface with standard tools, but firmware hacking can be complex. |
| Design-In DRAM Modules | Full DRAM modules (like SO-DIMM, industrial/embedded boards). | Not for direct dumping, but can be attacked with side-channel/fault methods. |
| Industrial microSD | Removable flash storage card in microSD form factor. | Very easy to dump with off-the-shelf card readers. |
| Industrial SD | Same as microSD but full-size SD card form factor. | Also easy to dump; common in industrial/embedded gear. |
Before proceeding with eMMC chip removal, stabilize the board to prevent accidental damage.

Inspect for faulty eMMC chips before removal:
Goal: Remove dust/flux residues for better heat distribution.
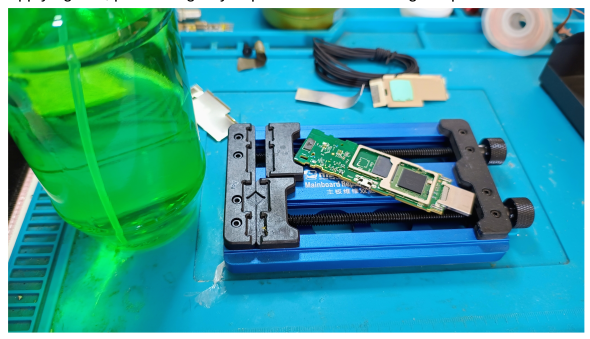
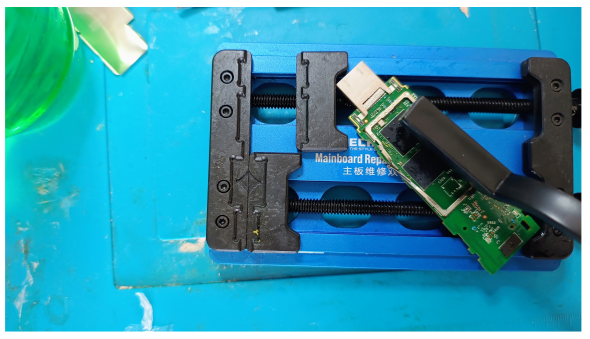
Purpose: Prevents oxidation, ensures proper solder wetting.

Why? Protects nearby components from heat damage.

Tools: Hot air rework station, thermocouple, tweezers.

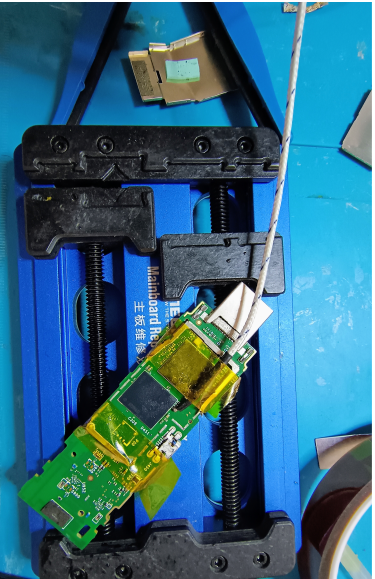
Goal: Clean PCB pads for reballing.
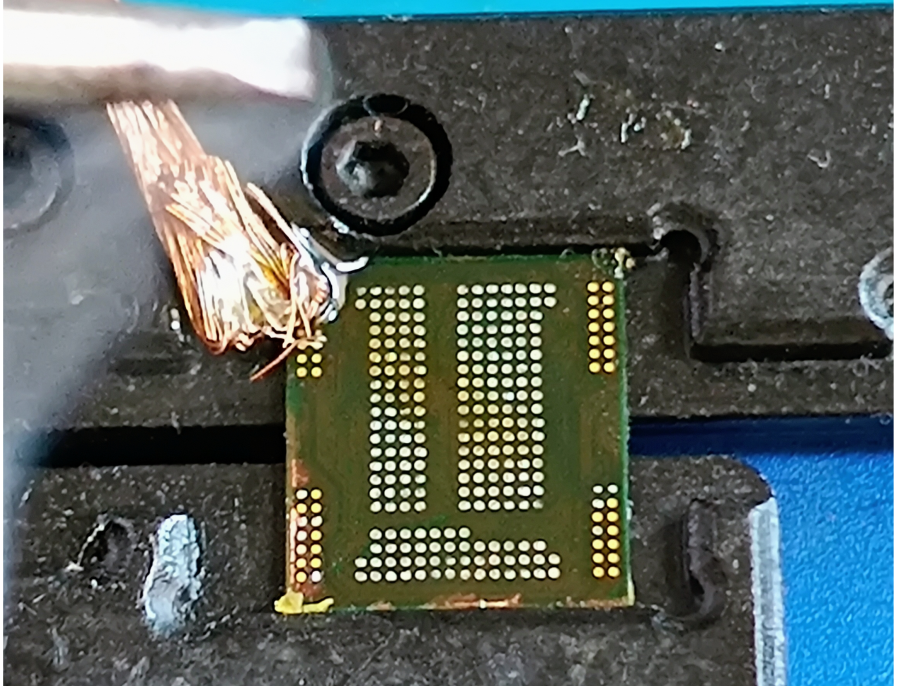
Steps:
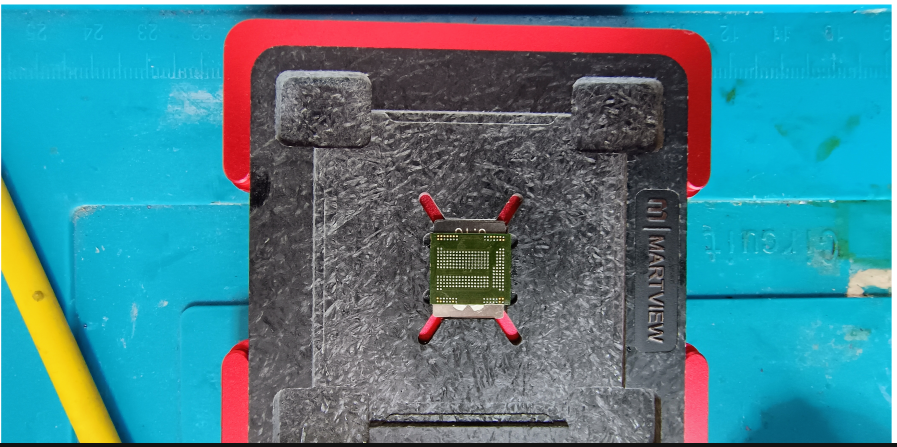


Method 1: Pre-made Solder Balls

Method 2: Solder Paste

Final Checks:
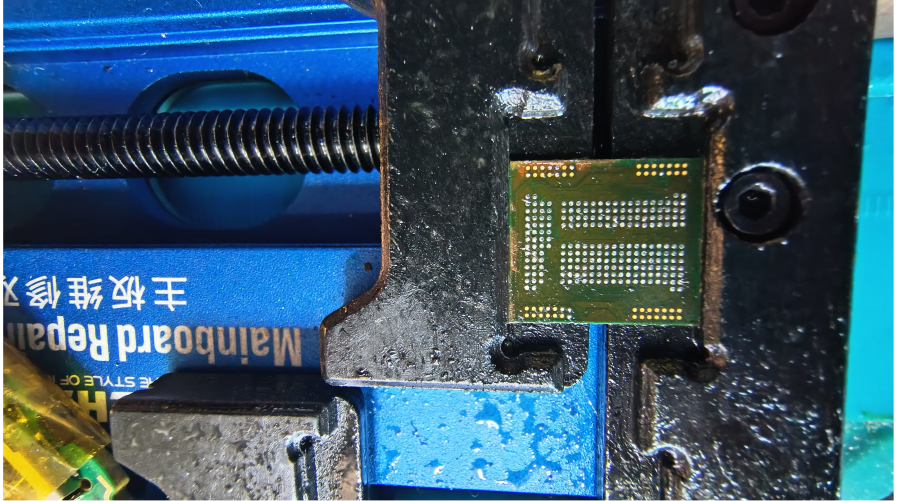

This concludes Part 1 of our eMMC/eMCP removal and reballing guide.
In Part 2, we’ll explore data extraction, adapter alignment, and dump analysis - critical steps for successful chip-off recovery and secure boot bypass attempts.
Always remember: this process is destructive and should be performed on test hardware only.